There are several forms of defining what are the applications in the context of networks of computers. In the model of reference OSI (Open System Interconnection) the application layer is the one that creates the interface between the network infrastructure and the insertion or reception of data. In this manner, the applications are directly responsible for receiving or sending the data that would traffic throughout the network.
Before this scenario, it is undeniable the importance of the applications for the functioning of the network. Departing of the principle of the strategical importance of the network for the business of a Company, the applications possess a crucial role for the daily routine of the companies.
Due to the strategical importance of the network it is indispensable to obtain an efficient management of your resources. Therefore, it is crucial to verify the existence of the applications which should not be trafficking in your network. As well as, those that are occupying a higher percentage than was previously though.
The TRAFip will provide a complete visibility of the network. As well as, the existence of non-certified applications. In the TRAFip the applications are categorized as an object. Thus, as such, can be enrolled, inserted in profiles, seen in reports and configured in alarms.
REGISTRATION OF APPLICATIONS
In the TRAFip it is possible to register applications utilizing the door, the IP or the ID of the application:
- Door: Main medium for the recognition of applications in the network. Mainly the most known ones, as for example: 80 (HTTP), 53 (DNS), 22 (SSH), among others…
- IP: Other mode of identification is the IP. So it is possible to identify applications hosted in specific servers.
- ID of the application: The TRAFip possesses the support and technology NBAR. In this manner, it is capable of identifying in a precise way the application by its ID in the NetFlow.
With applications registered immediately it is already possible to visualize the absolute chart of the traffic of every application. As well as, extracting reports.
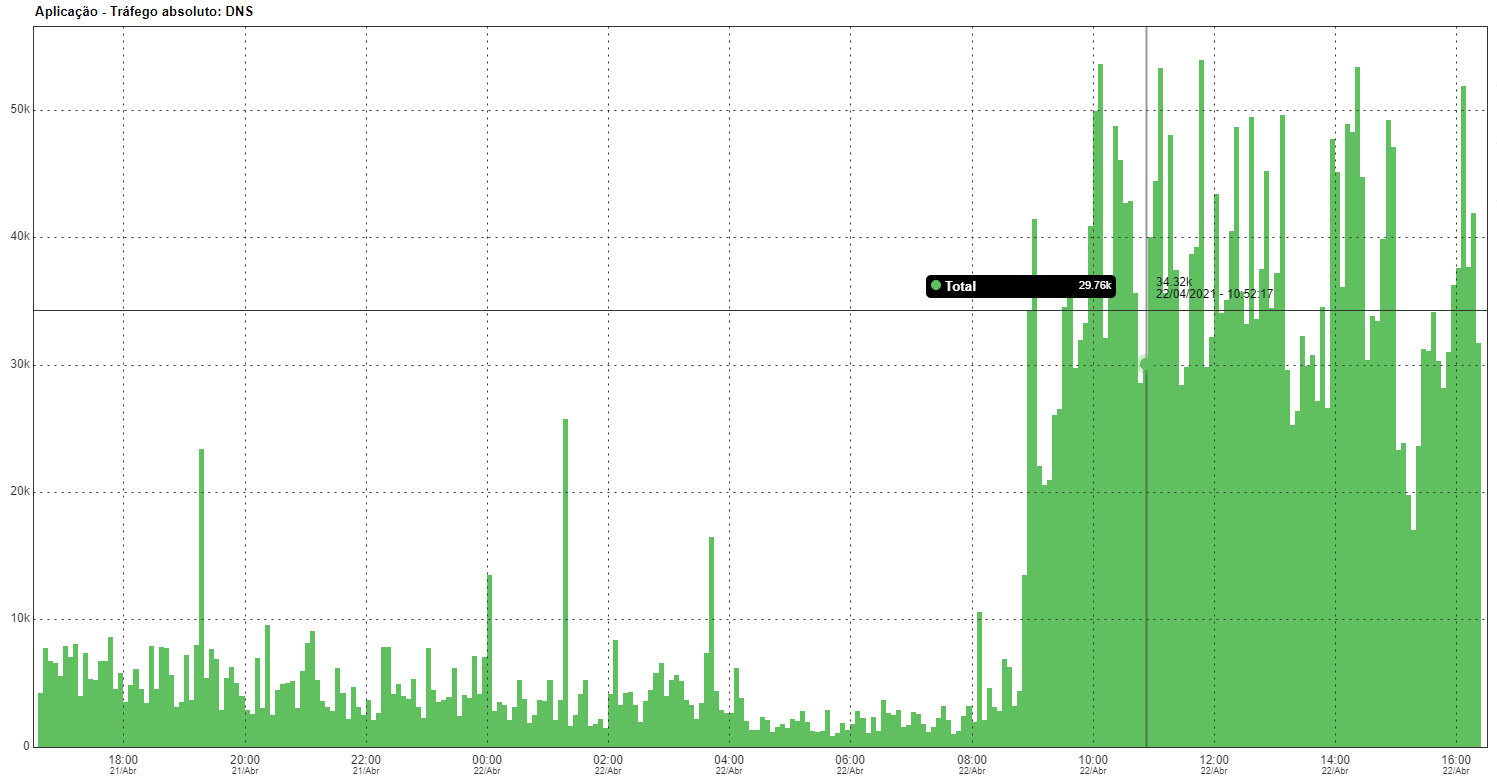
TRAFFICK PROFILE
The traffic profile is one of the main functionalities of the TRAFip. In this manner, it is possible to break the traffic of an object by another. Before this scenario, utilizing the application as object of profile, an example would be the break of the traffic of the subnetworks by application.
There are three forms of analysis of a profile of traffic: matrix, distribution and content. In order to utilize applications as profile object, the form of analysis will always be content. Mainly, for the fact that the application to be about the characteristics of the data that are trafficking.
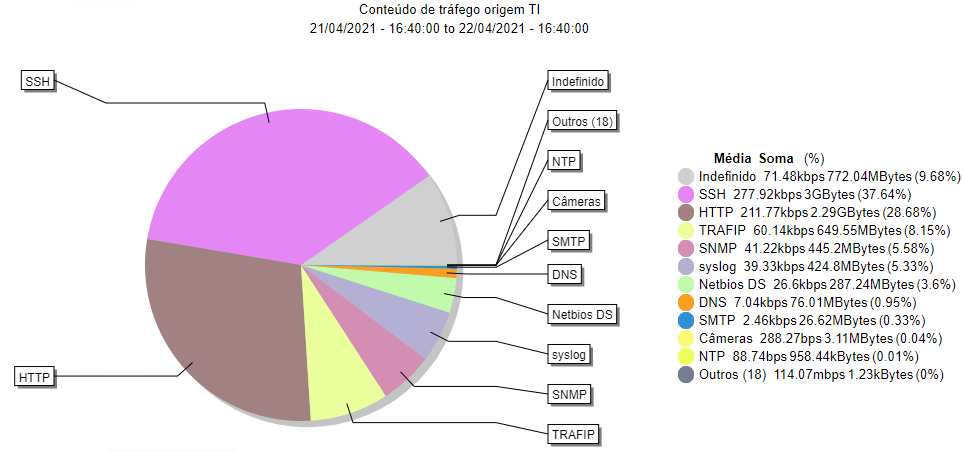
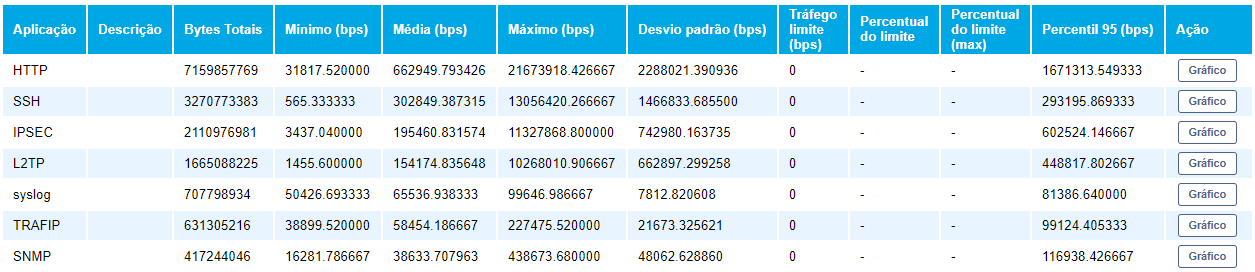
REPORTS OF TRAFFIC
For a greater drill-down of the behavior of the applications, the TRAFip disposes of a variety of reports such as: Top N characterized, Top N, raw data, traffic and projection profile.
The Top reports will rank the applications with higher traffic inside a specific period. Already the report of raw data will detail the fields of identification in relation to the flows collected, enabling inclusively the translation of each line of the report for the referring application. Another interesting option in the report of raw data is to enable the visualization of details in the traffic that has not yet been identified, such as the doors and IP addressing. Therefore, providing tools for updating the registers of applications that are not mapped.
The report of traffic profile, utilizing applications such as object of the profile, it will relate the application with another object of the network. Then the crossing of the chart will be the traffic of the object broken per application. Finally, the report of projection of the application will demonstrate the future traffic of the applications considering the current evolution.
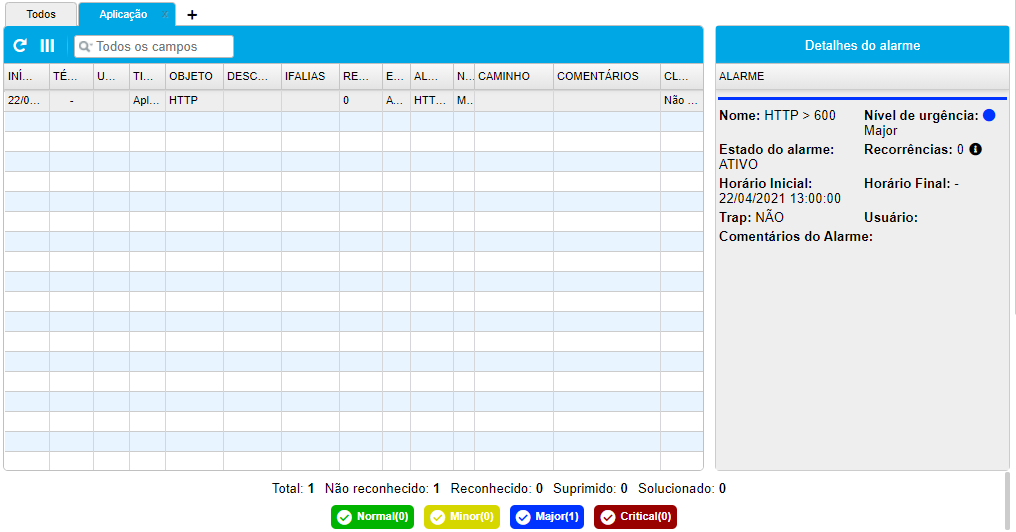
ALARMS OF APPLICATIONS
The alarms are crucial for any monitoring. Therefore, it can’t be different in relation to the applications. In the TRAFip, it is possible to configure limits of traffic for each application. Therefore, always when this limit is extrapolated, the user will be notified. The notification can be sonorous, by email, trap, SMS or even by the application Telegram.
Besides the standard alarms, there are also alarms for behaviors. Therefore, the user can be notified if inside a period the evolution of the traffic of some application, for example, violating that which was expected statistically.
FINAL CONSIDERATIONS
Besides applications, the TRAFip will provide the complete visibility of the traffic in relation to all the objects of your network.
In a nutshell, it gets practically impossible to respond to the question made in the title without the visibility of the network. TRAFip is a system of traffic analysis which allows the determining of what, how, when, where and by whom your network is being utilized.
In this sense, there is no doubts about the importance of having investments in network management. Bringing therefore not only benefits to the visibility of networks but also being a way to guarantee greater governance.
Thinking of that, Telcomanager present in the market since 2002, and a leading Latin America brand in the sector of software for managing networks. Also counting with a unique and innovative technology, deploying smart solutions in the monitoring of data that will provide a stratified vision of the traffic, is now allowing your Company to follow the most important aspects of your network, in real time.
 +55 (21) 3211-2223 info@telcomanager.com
+55 (21) 3211-2223 info@telcomanager.com