In the context of the infrastructure of computer networks, the conformity must be applied to the configurations of the devices. Independently of the environment we will have devices operating, whether if it is a big data center or in a small local network. Guarantee the connectivity with security and the good performance of the network is crucial, to get access to an internal application or even a cloud application.
Also, to guarantee that all the devices are configured in conformity with the policies of the IT infrastructure and of information security is primordial to achieve the objectives described above. However, how could we have such guarantee?
MANAGEMENT OF CONFIGURATIONS
“According to the FCAPS model created by the ISO, which divides the management of networks in five functional areas, the management of configuration has as a purpose to inventory the network. In this manner, discovering and monitoring the configurations of the objects. Therefore, orchestrating changes of configurations of assets with due agility.”
Excerpt taken from the article: https://www.telcomanager.com/blog/quanto-tempo-voce-gasta-para-configurar-os-seus-dispositivos-de-rede/
The management of configurations meet the need of having greater agility in changing the configurations of several devices simultaneously, to have full control of the versions of configurations of each device and guarantee the conformity of all the devices with the defined policies by the management of information technology and communication. For the examples of guaranteeing the conformity which is one of the pillars of configuration management we will quote some of the functionalities of the CFGtool.
REPORTS OF POLICY COMPLIANCE
One of the reports available in the CFGtool, is the report of policy compliance. In order to utilize this report, the first step would be to configure at least one rule. The rules will define what must include in the configurations of the devices so that they get in conformity with the respective policies. The rules can be configured in simple text, regular expressions or script. After the configuration of the rules, the next step is the creation of the policy, each policy can be associated to one or more rules.
Finally, for the generation of the report, it is enough to choose the devices and the policies which will be utilized for comparison. The report will signalize all the devices that are not in conformity with the policies. The reports can be scheduled to execute automatically in a period defined by the user. The result of the reports scheduled can be sent by email or to a FTP server.
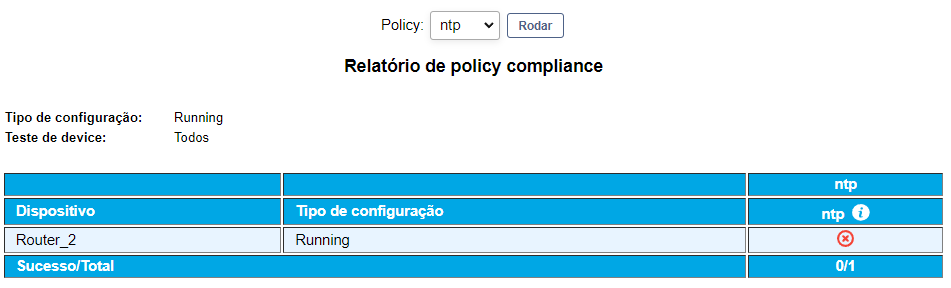
ALARMS OF POLICY COMPLIANCE
Besides the reports, alarms can be configured so that the users are notified when the devices are not in conformity with the selected policies. Every alarm can choose groups of selected users, the notifications can be performed by trap SNMP, via email, Telegram or even integrated to other systems utilized for the management of tickets or calls, it is valuable to highlight that for the latest, an analysis is performed to check and study the case.
In this form, we are able to guarantee the notification with the greatest agility possible so that all the devices possess all the configurations that are crucial for the information security and for the correct functioning of the network.
FINAL CONSIDERATIONS
CFGtool is a simple tool to use and with a great value for money. With remote and quick configurations, save time.
In this sense, there are no doubts about the importance of investing in network management. In this manner, it is perceptible that these good practices bring not only benefits for the visibility of the infrastructure, but also a way of guaranteeing crucial information for the governance of the network.
Thinking about it, Telcomanager, leader in Latin America in the sector of software for network management, since 2002 in the market with a unique and innovative methodology, makes available smart solutions for the monitoring of data for providing complete visibility to the infrastructure of the client, allowing your Company to accompany the main aspects of your network.
Posted on 02/25/2022
 +55 (21) 3211-2223 info@telcomanager.com
+55 (21) 3211-2223 info@telcomanager.com