Versioning is a procedure of controlling versions of configuration demonstrated through numbering. With that, guaranteeing that all the involved are able to know when and which alterations have been carried out, facilitating therefore, the following up of changes. All the alterations between the versions must be traceable with a clear indication of what was modified.
The versioning is considerably utilized for projects of software development, mainly due to the great demand for alterations and corrections in the code. With that, the property of accompanying each alteration and reverse it when necessary is crucial for the managing and control of the project.
In this article we will approach the concept of versioning applied to configurations of network devices. Primordially, its importance for the recovery of failures, identification of violations of conformity and correction of vulnerabilities.
MANAGEMENT OF CONFIGURATION
There is a diversity of configurations that can be applied in network devices, for several objectives, whether by reasons of security, connectivity control or for the improvement of performance. However, the more extensive the configurations, the greater the complexity of your administration. One recurring situation in several scenarios is the one that a network administrator seeks to discover a possible configuration error when he/she already has results in another problem, it can be expensive. Read the article: The cost of expecting for the problem to happen.
Failures of configuration can be responsible for considerable disasters in the functioning of the network, therefore, we can notice the importance of a good management of configurations. According to the FCAPS model created by the ISO, which divides the management of networks in five functional areas, the management of configuration has as a purpose to inventory the network. In this manner, discovering and monitoring the configurations of the objects. In this manner, performing the control of changes of configuration of assets with the due agility.
For the next topic of this article we will utilize the CFGtool for demonstrating how the versioning of the configurations of a network device is done. As well as, the options available for the identification of changes and guarantee of conformity.
VERSIONING OF CONFIGURATIONS
One of the tools found in the CFGtool is the summary of configurations of the device. For each equipment of network registered in the tool, the configurations will be stored and versioned. The checking of alterations of versions is done automatically through the system, in intervals defined by the user during the day.
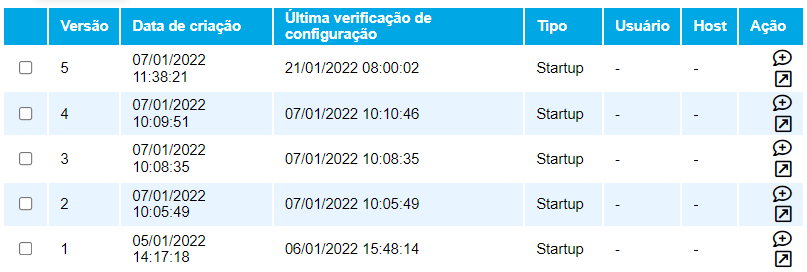
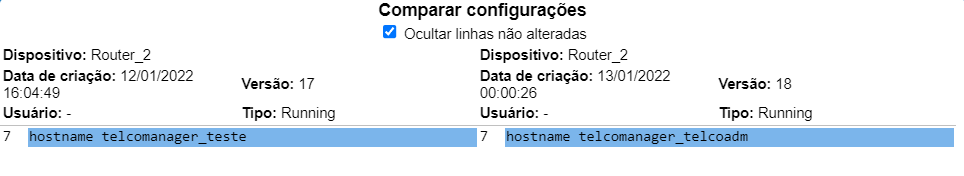
Imagine that the administrator of network is facing a severe problem in the functioning of one of the network devices, how useful would be to have a clear vision of what was modified in the configurations of the device before and after the occurrence. For that, it will be enough to choose two versions and compare.
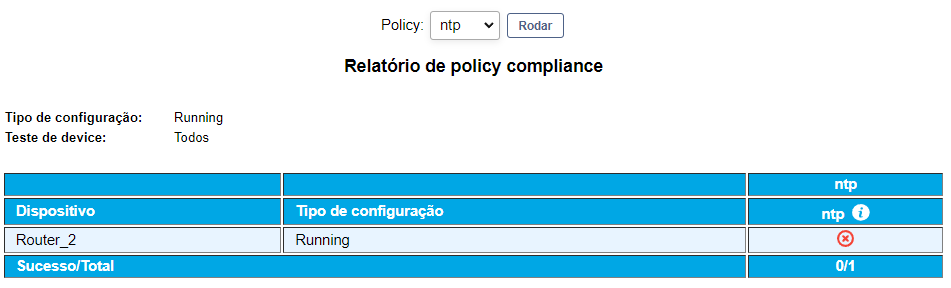
Now, the administrator wants to guarantee that the more recent version of the configuration of your device are in conformity with the infrastructure policies of TIC, such as, for example, if it possesses configurations referring to the NTP.
Finally, besides the possibility of performing the monitoring of the control of versions directly in the tool, it is possible to configure possible alarms to notify always that an alteration in the configuration of any device occurs or if any configuration does not obey to the defined policies. The alarms can notify through sound alerts, trap SNMP, e-mail, sms or Telegram.
FINAL CONSIDERATIONS
CFGtool is a simple tool to use and with a great value for money. With remote and quick configurations, save time.
In this sense, there are no doubts about the importance of investing in network management. In this manner, it is perceptible that these good practices bring not only benefits for the visibility of the infrastructure, but also a way of guaranteeing crucial information for the governance of the network.
Thinking about it, Telcomanager, leader in Latin America in the sector of software for network management, since 2002 in the market with a unique and innovative methodology, makes available smart solutions for the monitoring of data for providing complete visibility to the infrastructure of the client, allowing your Company to accompany the main aspects of your network.
Posted on 01/28/2022
 +55 (21) 3211-2223 info@telcomanager.com
+55 (21) 3211-2223 info@telcomanager.com